PUBLIC WIFI ATTACKS / MAN-IN-THE-MIDDLE (MITM) ATTACK.
When we visit any hotel or malls, we can see the Public Wi-Fi, nothing but Free Wi-Fi. To access the free wifi without a password we can access it by tapping on that wifi user name.
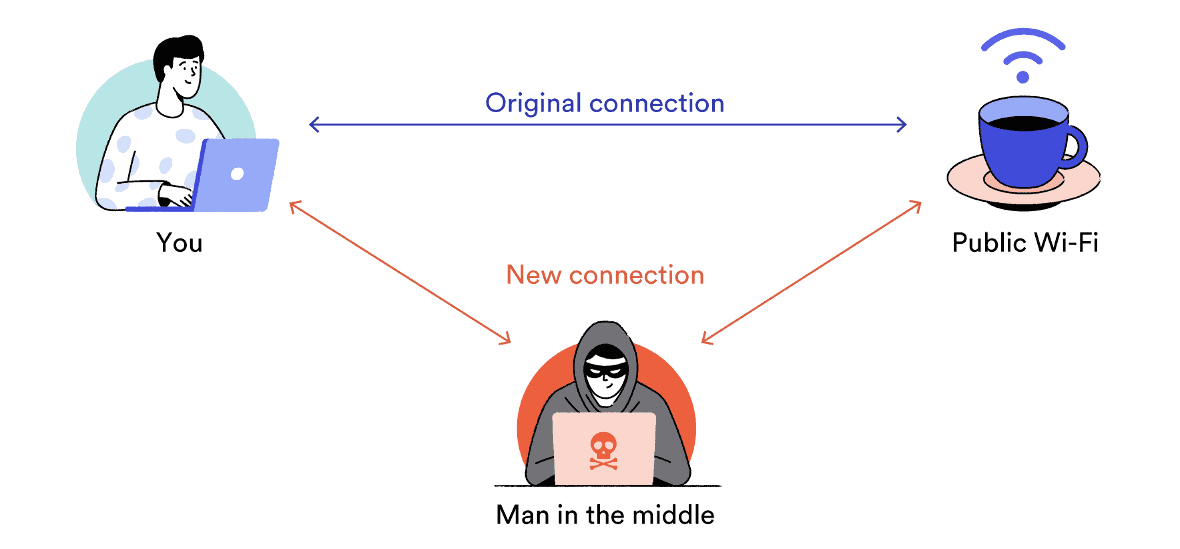
Many of us have access to those free Wi-Fi and chat with our friends, family, etc... We think that while we are exchanging the texts only 2 of us have the permit to the chats nut without our knowledge, there is a third person having access to all our phone activities.
Don't think that you are directly connected to the Wi-Fi and you are using if for 100% free. You are using Wi-Fi that's right but actually, you are connected to the third person and he connects you to Wi-Fi. He, the third person plays a key role in this attack.
These attacks are known as Man-in-the-Middle (MitM) attacks. The third person can see the entire conversation of your device. He can also send messages to your friends without your knowledge. We don't know what happens when we connect to public WiFi or free WiFi zones.
When we connect to the free WiFi or public WiFi the Man-in-the-Middle (MitM) attack takes place.
- Most of us, adopt free WiFi zones rather than the mobile data. We think why should we consume or waste our mobile data when i'm having access to the free WiFi. 99% of the population think the same.
- Let's see what happens when we connect to public WiFi or free WiFi zones.
- Our entire data gets compromised.
- Our phone gets Hacked.
- Malware, spyware, virus APK files may get installed without our permission.
- Our bank accounts and our social media accounts can be Hacked.
- Our Gmail passwords and recovery number can be changed.
- In simple words, our entire Phone will be controlled by the Hacker when we get access to the public WiFi which is not safe.
How do attackers hack if we are connected to the free WiFi or public WiFi :
- When we connect our phone to the public WiFi, then they use the IP address of our phone and they use the software which is the paid version, and generate the APK file in that software. They name it as Instagram or setting or anything else.
- A simple way to hack your phone when you connected to free WiFi is by attacking your wifi port's.
- Hackers use SYPNOTE software and other softwares which are paid. Once they create the APK file and the send it to your phone and when it gets installed then automatically that APK file gets disabled.
- When that APK file is installed on your phone, from then he can spy on you, he can monitor the entire phone, he can capture a picture of your face when you are using your phone and he will have access to these activities until he deletes your device from his computer.
Two Types of Public Wi-Fi
There are basically two kinds of public Wi-Fi networks: secured and unsecured.
An unsecured network can be connected to within range and without any type of security features like a password or login. Conversely, a secured network requires a user to agree to legal terms, register an account, to type in a password before connecting to the network. It may also require a fee or store purchase to gain access to the password or network.
Regardless of the connection type, you should always use Wi-Fi with caution. Now let's look at some dos and don'ts:
Do connect to secured public networks whenever possible. In the event that you're unable to connect to a secured network, use an unsecured network that would be permissible if the connection requites some sort of login or registration.
Don't access personal bank accounts, or sensitive personal data, on unsecured public networks. Even secured networks can be risky. Use your best judgment if you must access these accounts on public
Wi-Fi or not.
Don't leave your laptop, tablet, or smartphone, unattended in a public place. Even if your're working on a secure Wi-FI network, that won't stop someone from taking your property or sneaking a peek at your device.
Don't access to the WiFi which are not secured in the Bus stands, Railway stations, etc because we can't say that which WiFi is secured even they have the passwords but any WiFi can be compromised when hacker attack on it.
Don't shop online when using public Wi-Fi. Sure, shopping doesn't seem like it involves sensitive data, but making purchases online requires personal information that could include bank account and retailer login credentials. Shopping isn't something you want to do on an unsecured Wi-Fi network.
Do turn off automatic connectivity. Most smartphones, laptops, and tablets have automatic connectivity settings, which allow you to seamlessly connect from one hotspot to the next. This is a convenient feature, but it can also connect your devices to networks you ordinarily would not use. Keep these settings turned off, especially when you're travelling to unfamiliar places.
Do monitor your Bluetooth connectivity. Bluetooth in the home is an amazing feature on many smart devices. However, leaving Bluetooth on while in public places can pose a huge risk to your cybersecurity. Bluetooth connectivity allows various devices to communicate with each other, and a hacker can look for open bluetooth signals to gain access to your devices. Keep this function on your phone and other devices locked down when you leave your home, office, or similar secured area.
Do think about using a Virtual Private Network ( VPN) solution to ensure your privacy and anonymity are protected when you use public Wi-Fi. VPN services, like the new Norton Secure VPN, NORD VPN, can encrypt all the data that are send and receive while using a public Wi-Fi hotspot, securing your information from other users of the same connection.

If any cyber crime or any frauds happened to anyone then report to :
Follow us on Instagram for more updates.
If you have any questions/queries, do not hesitate to contact me.
@liferacer333 : https://www.instagram.com/liferacer333/?igshid=52f7yygpe2o1
If anyone is interested to start their career in Hacking, AI ( Artificial intelligences). Crypto technology then join in TCA ( The Cyber Agents) this platform gives you more knowledge and more information about these things : https://thecyberagents.com/






0 Comments