These are the types of cyber attacks which are done by the hackers to steal the information from our systems, servers, etc.....
Phishing
Viruses and Malicious Codes
UI Redress
Cookie Theft
Denial of Services (DOS/DDOS)
DNS Spoofing
Structured Query Language (SQL) Injection
Keylogger Injection
Brute Force
ClickJacking
QRLjacking
Tabnapping
Eavesdropping
Drive-by Attack
MALWARE
VIRUS
WORM
BOTNET
RAT ( Remote Accessing Trojan)
RANSOMWARE
Man-in-the-Middle ATTACK ( MitM )
1. Phishing :
- One of the most insidious techniques used today is Phishing. This is the basic tool which is used by the hackers to steal the account details by sending the link to the victims when we login to that link the entire account details like password, ip, IP address, mobile info, even it shows the network company to the hackers.
- Phishing implies the replication of the website with the aim to stealing money or personal information. And once a user enters his credit card details in that fake website, a hacker can get access to those details and will be able to use those information for his own benefits.
- Hacker will create the fake website it looks like real one but when we look original one but it is fake website. we think that this page is original and we enter all the details of our accounts then the entire information goes to the hacker.
- Phishing has different tools like: SHELLPHISH, SOCIAL PHISH, ZPHISHER, BLACEYE, etc....
- Social engineering is the technique it plays the major role in the Phishing attacks.Example X person generated the link and he send that link to Y person then, X person have to convince the Y person to login to that link like X person says that bro please login to that link i will get this much followers or this many links then automatically Y person will login then entire information will go to the X person in this way Social Engineering technique is used by the hackers to do steal your accounts.
Zphisher tool :
- this is what Zpshier this tool is used to do Phishing. to use this tool we have to type some commands then only this tool will run hackers will generate the tool and they will send that link to the victims when they login to that link then automatically the account details will be send to the hackers.
- This tool also similar to the Zphisher tool they will generate and they send the link.
SOCIAL PHISH TOOL:
- this tool mainly used to attack on the social media by sending the link to the victims we can get any social media account by generating the link.
- Phishing is the most famous technique used by the hackers to get the accounts information.
- even they can get access to your Gpay and phonepay accounts also when we click those links.
NOTE : never ever click any kind of links which you get in your whatsapp or any where because 90% cyber attacks are done by sending links to victims only one more thing if you get any links in HTTP format then you should not open that link HTTP format links are not secured attackers will steal your information when you open the HTTP links.
2. Viruses and Malicious codes :
- Hacker's can almost crawl into any website and leave in it's database malware or insert code into website files.
- There is a huge variety of viruses and each one may impact the infected websites differently.
3. UI Redress :
- This technique is similar to the phishing; but in this case a hacker could create fake hidden user interface.
- Once the user clicks that button with an intention of to proceed to a certain page he will find himself on an unfamiliar website. Usually,with inappropriate content.
4. Cookie Theft:
- With the help of a malicious software hackers can steal your browser's cookies containing a lot of useful login information, Usernames, passwords, browsing history. As you can understand that data can contain logins and passwords to websites administration's panel.
5. Denial of Services ( DOS/DDOS):
- DDOS stands for Distributed Denial of Service. DDOS attack is a way to make certain servers unavailable. Or in other words a way to crash the server.
- To interrupt or to crash the server hackers use bots. Those bots soul purpose is to send requests to the website, a lot of requests. As a result a server unable to process all of the received requests would simply crash the server. The most hazardous thing about this is that hackers could crash the server relatively in a small amount of time.
6. DNS Spoofing :
- This malware is also known as DNS cache poisoning. It engages that old cache data you might have forgotten about. Vulnerabilities in the domain name system allow hackers to redirect users from a user website to a malicious one.
- Moreover, hackers who can program this attack to this infected DNS server will infect another DNS and so on.
7. Structured Query Language (SQL) Injection :
- If your website has vulnerabilities in it's SQL database or libraries, hackers can get access to your confidential information by deceiving the system.
- so there is no surprise that SQL injections can also be a simple tool. But this tool can allow a hacker to access vital information of your website.
- By using this tool we can attack on any website.
8. Keylogger Injection:
- The keylogger has very simple and dangerous malicious codes.
- The malware auto records keystrokes, captures all of the users actions on the keyboard, and sends the information of your PIN to obtaining the data, then the result of the hacking will be stolen admin credentials that can allow hackers to easily log into your website.
- That's why we have to use the virtual keyboard where ever we go we should not use the normal keyboard. when we use the normal keyboard then the PIN number and details will be stolen. If we use virtual keyboard then no one can know our PIN number.
9. Brute Force:
- A Brute force attack is the simple method to gain access to a website. it tries various combinations of the passwords again and again until get's in. This repetitive action is like an army attacking a fort.
- By using brute Force we can hack the any account password.
10. Clickjacking :
- ClickJacking attack refers to any attack where the user is tricked into unintentionally clicking on a web page element.
- The name was coined from "Click Hijacking" and the technique is most often applied to web pages by overlaying malicious content over a trusted page or by placing a transparent page on top of a visible one.
- when the user clicks on an innocent-looking item on the visible page they are actually clicking the corresponding location on the overlaid page and the click triggers a malicious action anything from a faking a like or a follow on social media to siphoning money from the users bank account.
11. QRL jacking :
- QRL Jacking is an attack in which an attacker creates a fake QR code.
How does it work?
- The attacker initializes a client side QR session and clones the login QR code in to a phishing page.
- The attacker then sends the phishing page to the victim. If convinced the victim scans the QR code with a specified targeted mobile app.
- The mobile app sends the secret token to the target service to complete the authentication process.
- As a result, the attacker who initializes the client side QR session gains control over the victim account.
- Then the service starts exchanging all the victim's data with the attackers browser session.
"The attacker needs to initialise a successful QRL jacking attack is to write a script to regularly clone the expirable QR codes and refresh the ones displayed on the phishing website which they created. As we know that a well implemented QR login process should have an expiration interval for the QR codes".
- An attacker can exploit the QRL jacking to take over accounts for services that rely on vulnerable QR-Code-Based login authentication.
- For further information hack a look on this github.com( QRL-JACKING)
- Don't scan the QR codes in the public even when you purchase anything because when we scan the QR code then the information of our bank accounts or our whats app will be controlled by the hackers.
- So many cases are registered regarding this QR code attack only. Kindly i'm requesting you not to scan the QR codes.
- Mostly avoid this scanning of QR codes how many times you scan the QR that many times your money will be stolen from your account.
12. Tabnapping:
- Tabnapping a type of social engineering attack where the attacker replaces the contents of a dormant browser tab with a spoofed website intended to collect passwords or other sensitive information.
- This type of attack would rewrite the existing tab with the attackers website. Wherever the victim comes back to that tab, he will think that he has logged out of that particular website and try to login again, and as soon as the victim logs into his account, the attacker will capture the credentials. The SET can be used to launch this attack.
13. Eavesdropping :
- Eavesdropping is an electronic attack in which digital communications are intercepted by an individual whom they are not intended to.
- This is done in two main ways: Directly listening to digital or analog voice communication or the interception or sniffing of data related to any form of communication.
- It is the act of intercepting communication between two points.
- Actually, Eavesdropping is nothing but listening to other people talk without knowing them. It can be done using current technology such as hidden microphone and recorders.
- Devices with microphones including laptops and cellphones also can be hacked to remotely activate their microphone and discretely send data to the attacker.
14. Drive-by Attack :
A Drive-by Attack is a common method of distributing malware.
- A cyber attacker looks for an insecure website and plants a malicious script into PHP or HTTP in one of the pages. This script can install malware into the visitors computer who visits that particular website or become an IFRAME that redirects the victim's browser into a site controlled by the attacker.
- This attack is known as Drive-by Attack because they don't require any action on the victim's part. Except visiting the compromised site.
- When they visit the compromised site they automatically become infected if their computer is vulnerable to the malware, especially if they don't take any security precautions such as updating their system/Apps etc.....
15. Malware :
- Malware is an software intentionally designed to cause damage to a computer,server, client or computer network. A wide variety of malware types are exist, including computer viruses, worms, Trojan horses, ransomware,spyware,adware,rouge software and scareware.
- Malware are most affected once when it get install in our computer then our entire system will be collapsed our system will be controlled by the hackers he may do illegal things from our system also.
16. VIRUS :
- Virus is the infected file or software, when it enter into our system then it disturb the computer software it will not allow out computer to work.
- It will also corrupt the files in our system when our files get corrupted then those will not open.
NOTE : Use anti-virus in your systems like how helmet protects the bike rider from the accident same in computer also anti-virus will provide the security to our system from the attackers or malicious software it will not allow those infected files or apps to our system.
17. Worm :
- A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it.
- It will use this machine as a host to scan and infect other computers. When worm enter into server or computer which belongs to a particular company then it runs automatically.
- To run the worm we no need to type any command when it is installed then automatically it starts it work and it totally destroys the servers and computer which are connected to the same internet or same port.
18. BOTNET :
- A botnet is a collection of internet-connected devices infected by malware that allow hackers to control them. Cyber criminals use botnets to instigate botnet attacks, which include malicious activities such as credentials leaks, unauthorized access, data theft and DDOS attack.
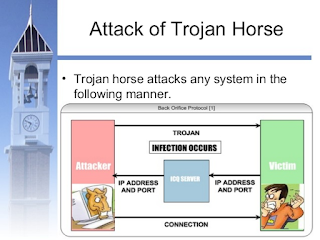
19. RAT ( Remote Accessing Trojan) :
- A trojan horse or Trojan is a type of malware that is often disguised as legitimate software. Trojans can be employed by cyber-thieves and hackers trying to gain access to users systems.
- Users are typically tricked by some form of social engineering into loading and executing trojans on their systems.
- There trojans will enter into our computer when we download the malicious software of files which are already affected with these trojans.
- When RAT attacks takes place then our entire system will be out of control we can use our computer for our use and from other face the attacker will use your system to do his works like he will use your internet for send any thing to other persons also.
20. RANSOMWARE :
- Ransomware is a type of malicious software, or malware, designed to deny access to a computer system or data until a ransom is paid. Hackers will install the malicious software when they install that software then entire computers which are connected to that server will not work.
- The entire system will be locked until we pay the amount which was asked by them. The amount should be given in the bitcoins only they ask them to pay in bitcoin other than bitcoin they don't take it .
- That's why some companies will keep their DATA as backup they will store their data in other servers if any cyber attack takes place then they use the data which they kept for backup.
21. Man-in-the-Middle (MitM) Attack :
- Man-in-the-middle attack is the most commonly done by attacker's. how this attacks takes places:
- when we use Public WIFI or Free WIFI.
- when we use Public Charging Ports.
- when we download malicious softwares.
- If we click any links or download any APK files then this attack takes place our entire phone will get compromised.
NOTE : PLEASE USE ANTI-VIRUS IN YOUR SYSTEMS. ANTI-VIRUS WILL PROTECTS YOU FROM THE MALICIOUS FILES AND SOFTWARE'S. DON'T USE FREE ANTI-VIRUS USE PAID ONCE FREE ANTI-VIRUS DON'T PROVIDE THAT MUCH SECURITY TO YOUR SYSTEM RATHER THAN PAID ONCE.
Follow us on Instagram for more updates and if you have any doubts you can ask us.
@lifeacer333 : https://www.instagram.com/liferacer333/?igshid=52f7yygpe2o1
If any one is interested to start their career in hacking, AI ( Artificial Intelligences ), Crypto technology then join in TCA ( The Cyber Agents) this platform gives you more knowledge and more information about this things : https://thecyberagents.com/

























0 Comments